The weapons that decide tomorrow’s wars will manipulate signals, blind radars, and mislead guidance systems. These are the tools of electronic warfare that will shape the strategic balance for years to come and will become the decisive factor in future military conflicts. The reason is relatively straightforward. Modern militaries fight as networks of sensors, shooters, and decision makers. And whoever controls the electromagnetic spectrum controls that battlefield.
In this article, I’ll explain why electronic warfare is becoming the core of modern defense strategy, what technologies matter, and how doctrine is changing. The goal is practical foresight for policymakers, business operators in defense and telecom, and strategists who need a clear picture that connects technology with power and outcomes.
What Electronic Warfare Covers and Why It Matters
For starters, electronic warfare (EW) refers to using the electromagnetic spectrum to detect, deceive, disrupt, or destroy an adversary’s ability to communicate and operate effectively. It spans three functions:
- Electronic Support (ES) identifies, collects, and locates electromagnetic emissions for awareness and targeting.
- Electronic Attack (EA) disrupts, deceives, or destroys adversary systems with jamming and spoofing.
- Electronic Protection (EP) shields friendly systems from adversary EW and keeps the lights on under fire.
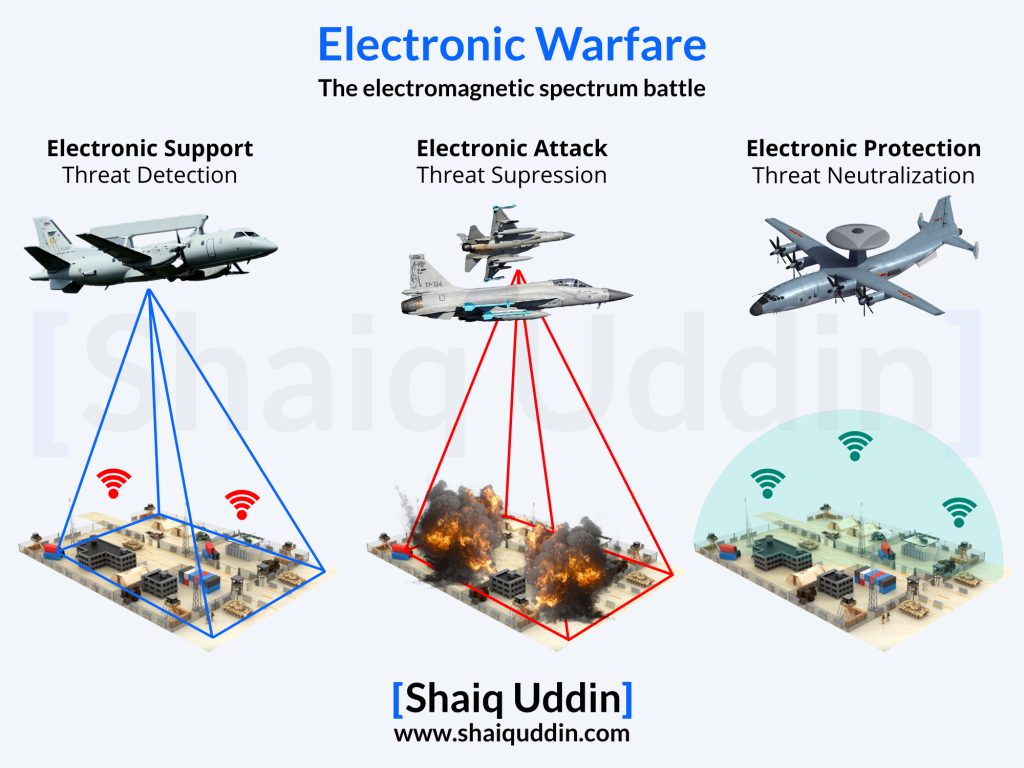
What makes EW unique is that it is not limited to a single platform or weapon. It is integrated across air, land, sea, space, and cyber operations, creating a force multiplier for every other domain. It touches satellite communications, GPS, radars, data links, drone control, and even civilian aviation. The 2019 India-Pakistan air skirmish and the Russia–Ukraine war are recent examples of how EW will play a much more significant role in future wars.
The strategic implications are simple. If a force cannot trust location, timing, and communication, it loses tempo and precision. If it regains spectrum control, its weapons and sensors recover their advantage. That is why senior US commanders warn that failing to win the EW fight means the joint force “loses very quickly,” as mentioned in this Business Insider article.
Why EW Has Moved to the Center of Strategy
Electronic warfare is no longer just about jamming radios and is certainly not a support function anymore. It is shaping the entire operational environment, from how forces communicate to how weapons find and lock their targets. I’ll break this down into four points to explain how EW has become decisive and why it is now non-negotiable for any serious military power.
1) The modern kill chain depends on fragile links
Precision warfare relies on tight sensor-to-shooter chains. To simplify, this chain is built on several interdependent layers. At the sensing layer, radars, passive RF sensors, and satellites collect data about potential targets. At the networking layer, secure data links and relay systems move the targeting information to the units capable of engaging the threat. At the positioning layer, Global Navigation Satellite Systems (GNSS) like the GPS or the Chinese BeiDou navigation deliver the precise coordinates and timing that modern munitions require to strike accurately. Together, this makes an entire kill chain.
Below is a visual representation of an F2T2EA military kill chain model:
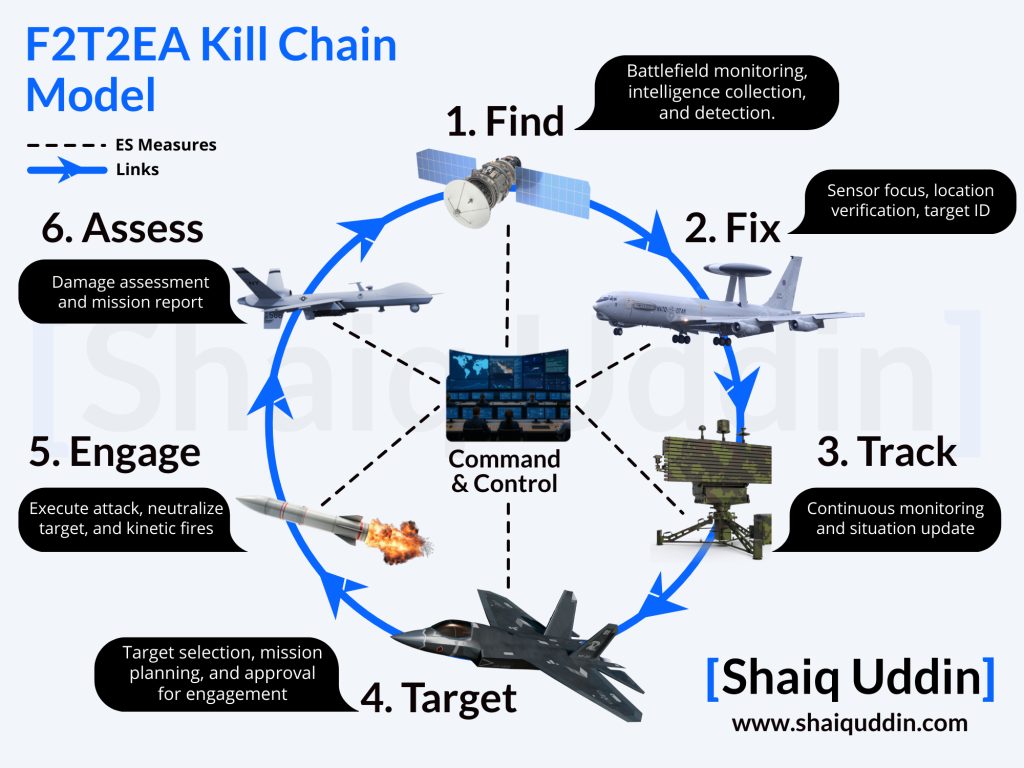
If the enemy’s EW suite breaks the kill chain, even the most advanced platforms become expensive hardware vulnerable to an attack. We’ve seen how Russia’s fielded electronic warfare systems have degraded the accuracy of several US-supplied weapons and rocket artillery to Ukraine by attacking those data links with jamming and spoofing. This means that survivability in future wars will depend on whether a force can keep its kill chain intact under sustained electronic attack.
2) Cyber and EW now overlap
Cyber warfare traditionally targeted software, exploiting vulnerabilities in code to gain unauthorized access or cause disruption. Similarly, EW systems were used to target electromagnetic signals that carried information. But in today’s battlespace, these two domains seem to be converging. An adversary can attack a system’s software via its signal pathways and, conversely, manipulate its signals to exploit weaknesses in the software layer.
For instance, an attacker can inject false radar tracks into an air-defense network, making it appear that incoming aircraft are approaching from the wrong direction. A drone’s unencrypted control link can be intercepted and overridden, allowing an adversary to seize control mid-flight. Even systems with encrypted links can be subjected to denial-of-service attacks through targeted jamming, forcing them into fallback modes where other vulnerabilities can be exploited.
The most visible convergence of cyber and EW is in counter-drone warfare. Radio jamming, GPS spoofing, and software exploits are deployed together to neutralize incoming drones. The defense system might first jam the drone’s GNSS signal to force it into “return-to-home” mode, then spoof its control link to redirect it into a trap. This level of integration shows that cyber and EW are merging into a single operational discipline.
3) A2/AD relies on spectrum denial
Anti-access/area denial (A2/AD) strategies are designed to prevent an adversary from operating freely in a contested zone. Historically, these strategies relied on long-range missiles, air-defense networks, and overlapping fields of surveillance. Now, electronic warfare is the binding agent that makes these layers effective.
A 2023 special report published by the Royal United Services Institute (RUSI) revealed some interesting points on this particular topic. It explained how Russia uses its EW systems to create “electromagnetic exclusion zones” where GNSS is unreliable, communications are intermittent, and radar performance is degraded.
For defenders, this forces tactical adaptation. Routes and flight plans must be changed to skirt jamming fields. Timing must be adjusted to exploit windows when EW coverage is lighter. And equipment must be upgraded with electronic protection features to operate in degraded environments. The challenge for offensive forces is that every adjustment slows their tempo, while the defender’s A2/AD posture remains intact. This is why spectrum denial is becoming as important to A2/AD as physical defenses.
4) Civil systems will be contested
In 2024, the European Union Aviation Safety Agency (EASA) issued a safety information bulletin to address GNSS interference near active conflict zones. Airlines were instructed to train pilots on navigation procedures for GPS-denied environments. Airports reviewed contingency plans for instrument approaches when satellite navigation is unreliable. Aircraft manufacturers began incorporating more robust multi-sensor navigation suites to maintain accuracy when communication signals are degraded or spoofed.
This is a serious concern because the line between civil and military effects is becoming thin. It means that states can now impose economic and logistical friction without ever firing on a civilian target. By simply deploying electronic warfare systems near contested borders or maritime chokepoints, they can subtly disrupt shipping schedules, delay flights, and create uncertainty in trade flows, all while remaining below the threshold that would trigger a formal military response. In future conflicts, the ability to control or disrupt civil systems will be as much a tool of statecraft as any formal sanction or blockade.
Technology Shifts That Will Define the Next Decade
I watch the shifts in electronic warfare and sensing technology closely because they are redefining military operations’ speed, reach, and resilience. Over the next decade, these four technological developments will likely change how modern forces fight and reshape the balance of power in every domain across land, air, sea, cyber, and space.
AI-driven spectrum operations
It’s a known fact now that artificial intelligence is already reshaping how militaries detect, classify, and counter threats in the electromagnetic spectrum (EMS). Machine learning algorithms identify signals, pinpoint their origin, and even choose jamming or deception tactics faster than human operators can react. This shift from human-led decision-making to machine-speed operations means that electronic support (ES) and electronic attack (EA) cycles will compress to milliseconds in high-intensity conflicts. That’s the same leap cyber defense made when automated intrusion detection systems replaced manual log reviews.
RAND’s 2023 report on EMS competition warns that adversaries are designing more agile and adaptive systems to evade legacy detection and jamming. These systems may alter frequency, power, and waveform in real time to avoid being locked onto. The countermeasure will be faster and powerful AI models that learn and respond dynamically, effectively running a continuous cat-and-mouse game at machine speed. This is similar to adaptive cyber defense, but in the RF spectrum, where milliseconds matter.
Disaggregated and distributed EW
For decades, most advanced EW systems and capabilities were concentrated in specialized platforms or aircraft known as AWACS. But last year, reports emerged that the U.S. Air Force (USAF) is quickly pivoting toward “disaggregating” EW from these high-value platforms and pushing it across diverse carriers, from fighter pods to expendable drones, unmanned maritime craft, and even ground vehicles. The primary goal for this shift is to increase survivability by ensuring no single platform or asset becomes a critical node whose loss cripples EW capability during an active conflict.
Distribution also means effects can be delivered closer to the tactical edge. Instead of relying on one or two large EW aircraft orbiting far from danger, small, low-cost unmanned systems can operate deep inside contested airspace, jamming or deceiving enemy radars at standoff range. This approach forces adversaries to allocate more resources to detect, track, and neutralize multiple, unpredictable EW nodes.
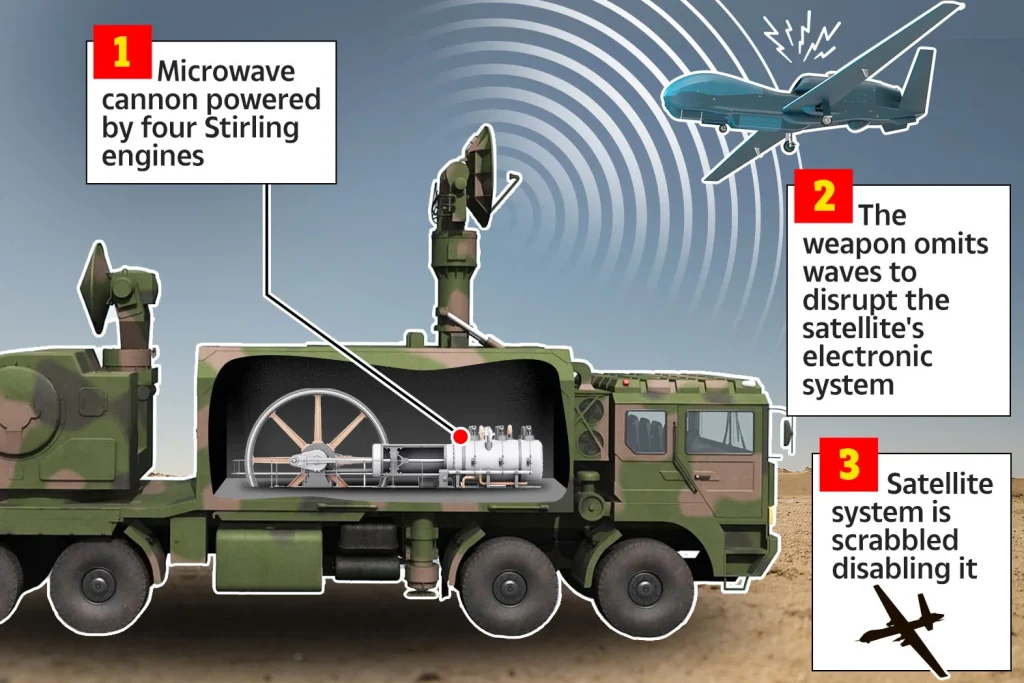
Directed energy weapons (DEWs)
DEWs are high-energy lasers and high-power microwave (HPM) systems now emerging as a key bridge between electronic attack and kinetic strike. HPM systems can disable the electronics of drones, cruise missiles, or radar systems without physically destroying them, making them a practical option for defending against massed incoming threats. Unlike electronic jamming, which can be countered with spectrum agility, a microwave pulse can physically disrupt or destroy sensitive electronics of any weapon.
 (Image source: The Sun News)
(Image source: The Sun News)
The economics are compelling. A microwave shot can cost a fraction of a missile interceptor, making it viable for defending against drone swarms or saturation attacks. As adversaries increasingly field cheap, disposable unmanned systems, DEWs offer a scalable, low-cost-per-shot defense layer that complements both EW and traditional air defense. Modern militaries like China and Russia are accelerating HPM field tests for base defense and shipborne applications.
Satellites and Space as a Target
Historically, satellites provided essential services like satellite communications (SATCOM), weather imagery, and positioning, navigation, and timing (PNT). Then, over the last few decades, we saw how they became a tool for military operations by hosting EW payloads capable of detecting, geolocating, and even jamming signals from orbit. Electronic warfare now extends beyond Earth’s surface.. This enables global-scale coverage, supporting operations anywhere in the world within seconds. For example, space-based SIGINT satellites can cue airborne or ground EW assets in near real time.
However, space systems themselves are becoming contested. Ground stations, satellite uplinks, and even satellites are vulnerable to jamming, spoofing, or disruption. The interplay between space and electronic warfare creates a dual challenge for nations that must now protect their space-based assets while upgrading them for EW advantage. Air Forces and armies are experimenting with uplink jamming to disrupt SATCOM or insert false data into navigation signals. The spillover into civilian domains, such as disrupting maritime GPS or telecom services, adds another layer of geopolitical risk that must be managed.
The Business Angle: Where Value Will Be Created
I see the rapid advancements in electronic warfare from both the defense and business perspectives. From startups innovating modular jamming pods to telecom giants hardening networks, the need for resilient communications, navigation, and spectrum control will open multi-billion-dollar opportunities. Whether in defense, manufacturing, or telecom, the winners will be those who can deliver adaptable, interoperable, and commercially viable EW solutions faster than competitors.
Telecom and Connectivity Providers
Telecom operators and connectivity providers sit at the center of the EW risk equation because their networks depend on spectrum integrity. That means, even minor disruptions can cascade into customer dissatisfaction, safety hazards, and revenue losses. As 5G, satellite internet, and private industrial networks spread into ports, factories, energy sites, and transport corridors, the surface area for RF interference and GNSS disruption will likely expand, making these businesses vulnerable and high-value targets. Similarly, the aviation and maritime sectors are already adjusting to increased GNSS interference, with aviation safety bulletins and operational mitigations, which signal that resilience is becoming a commercial differentiator for connectivity.
The business opportunity here can be found in creating premium connectivity tiers that guarantee performance even under contested environments. Like the cloud industry, which monetizes uptime guarantees and sells Service Level Agreements (SLAs), telcos could monetize “resilient connectivity” and offer a productized service that includes monitoring, rapid anomaly detection, and failover options. This would allow them to charge a premium to industries where every second of downtime translates into millions in losses. Aviation operators that depend on uninterrupted signals for navigation, shipping companies coordinating global fleets, and logistics hubs synchronizing container movements are among the most likely to adopt these higher-value services, since these are industrial customers with high outage costs and would be willing to pay for this kind of assurance.
In the satellite and wireless connectivity space, interference monitoring and geolocation are everyday functions. For example, many satellite operators utilize systems like Monics to precisely trace RF interference sources, which are part of Network Operations Center (NOC) toolsets used worldwide. Although these capabilities are not yet framed as EW-specific mitigations, they lay the technical groundwork for resilience solutions. Providers that bundle such existing tools into audited, “assured connectivity” offers will likely lead the market in the near future and achieve recurring, premium revenue streams.
Defense Contractors and Startups
In defense, the big-ticket EW offerings from major Western contractors like Raytheon, Northrop Grumman, and BAE Systems will continue, but agility is becoming more valuable than sheer scale. The competitive advantage is now in rapid software updates, AI-based electronic support (ES) capabilities, and open architectures that allow seamless waveform and protocol changes. This is particularly true in coalition environments where interoperability is critical. For example, NATO’s 2024 Thor’s Hammer exercise demonstrated that systems unable to integrate and adapt under contested spectrum conditions lose operational value, regardless of hardware sophistication.
For defense startups and manufacturers, especially those working in electronic warfare systems, the opportunity lies in modularity and niche applications. Portable EW pods that can be mounted on drones, ground vehicles, or small ships are gaining traction, especially if they can be easily updated with new threat libraries. Counter-unmanned aerial systems (C-UAS) remain a hot market segment, and hybrid systems combining soft-kill (jamming, spoofing) and hard-kill (kinetic interceptors, directed energy) approaches are attracting military and security buyers who want layered defense solutions. Moreover, the lower entry costs for software-based ES tools can also open the door for innovative startups to win contracts for tactical RF mapping and interference geolocation.
One crucial factor I’d like to mention here is the speed of delivery, which is becoming a decisive factor in military procurement. Military customers are increasingly bypassing slow, multi-year acquisition cycles in favor of commercial-off-the-shelf (COTS) solutions that can be customized and adapted for operational use in months. That means startups that can integrate into open EW architectures and provide immediate, interoperable capabilities will have a chance to secure early contracts and even long-term strategic partnerships.
Cloud and Data Center Operators
Cloud providers and data center operators are also exposed to EW risks, though in less obvious ways that go beyond traditional cyber or physical threats. As their infrastructure runs on precise timing, studies have shown that even minor GNSS disruptions can lead to latency spikes, failed transactions, or broader synchronization errors. For operators, such downtimes could directly hit their customer trust and reputation in industries where latency or failures carry heavy financial penalties. That is why modern data centers are considering deploying multi-source timing strategies by combining GPS, atomic clocks, and network time servers to mitigate this risk and ensure continuity even if one input fails.
However, this risk exposure also creates an opportunity to monetize resilient cloud infrastructure that integrates localized timing sources and atomic clocks. Enterprises in finance and media would be willing to pay premiums for cloud regions and colocation facilities that offer certified resilience against GNSS disruption. For example, Equinix offers Precision Time, which is a time as a service application providing interference-resilient timing feeds to customers who cannot afford synchronization failures. This is a similar model to AWS GovCloud for compliance-driven workloads, where cloud providers can convert a technical safeguard into recurring revenue streams.
But in the longer term, differentiation will come from expanding resilience into edge computing markets, which is particularly useful for applications that require real-time responses, such as autonomous vehicles, industrial automation, and smart healthcare. EW risks in this particular domain mean more operational and financial risks for businesses. Therefore, cloud providers who can build EW-aware, multi-source timing into their edge services can attract new customers in sectors where even minutes of disruption equal huge financial losses. Early movers can lock in enterprise trust, regulatory approval, and a leadership position in what will become a premium category of “resilient cloud.”
Final Thoughts: Where is this heading?
When I look at the advancements in electronic warfare systems today, they are no longer confined to military domains. I see a shift that touches every industry, every critical infrastructure, and every digital system we rely on. EW has moved from being a hidden layer of defense strategy to a visible threat for telecom networks, data centers, power grids, and other sectors at the frontlines of resilience. The consequences could shake an entire economy if these systems fail during a major EW attack.
Resilience against EW risks is fast becoming a baseline expectation, much like cybersecurity did over the past two decades. That shift will unlock new business models, premium service categories, and stronger regulatory frameworks. Both startups and established players have the chance to shape this emerging market by embedding resilience directly into their products and operations. And those who act early will set the standards others follow.
For me, the real opportunity lies in bridging national security imperatives with business value creation. Countries and companies that treat EW systems as a strategic tool and EW resilience as a competitive advantage will strengthen their assets and capture market trust and long-term economic influence. The winners of the next decade will be those who can defend their networks, infrastructure, and reputation while keeping entire economies running. That’s the future I see, and it’s where the defining opportunities of our era will emerge.

